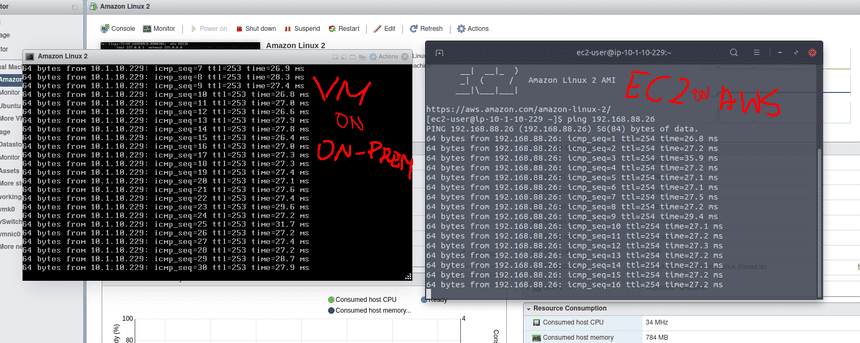
Configured on the Mikrotik 6.45
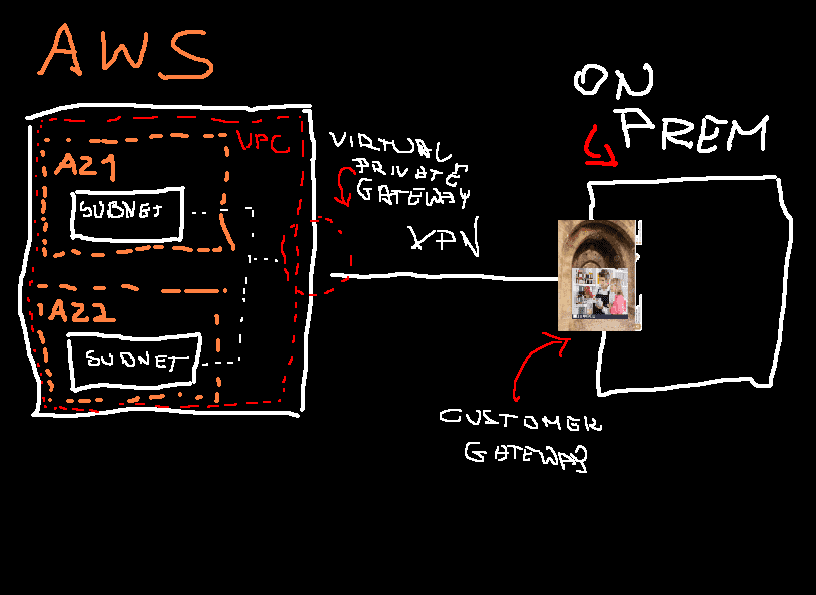
AWS VPC - 10.1.0.0/18
AWS Private Subnet 1 - 10.1.1.0/24
AWS Private Subnet 2 - 10.1.2.0/24
On-Premise Subnet - 192.168.88.0/24
---
AWSTemplateFormatVersion: "2010-09-09"
Parameters:
PublicIP:
Type: String
Description: "Public IP address of the on premise"
OnPremiseSubnet:
Type: String
Description: "Subnet in the on premise network"
Resources:
VPC:
Type: AWS::EC2::VPC
Properties:
CidrBlock: 10.1.0.0/18
EnableDnsSupport: true
Tags:
- Key: Name
Value: VPN AWS & on prem
PrivateSubnet01:
Type: AWS::EC2::Subnet
Properties:
AvailabilityZone: !Select
- 0
- Fn::GetAZs: !Ref "AWS::Region"
VpcId: !Ref VPC
CidrBlock: 10.1.10.0/24
Tags:
- Key: Name
Value: "[PRIVATE-01] VPN AWS & on prem"
PrivateSubnet02:
Type: AWS::EC2::Subnet
Properties:
AvailabilityZone: !Select
- 1
- Fn::GetAZs: !Ref "AWS::Region"
VpcId: !Ref VPC
CidrBlock: 10.1.20.0/24
Tags:
- Key: Name
Value: "[PRIVATE-02] VPN AWS & on prem"
RouteTable:
Type: AWS::EC2::RouteTable
Properties:
VpcId: !Ref VPC
Tags:
- Key: Name
Value: VPN AWS & on prem
RouteTableAssociatePrivateSubnet01:
Type: AWS::EC2::SubnetRouteTableAssociation
Properties:
SubnetId: !Ref PrivateSubnet01
RouteTableId: !Ref RouteTable
RouteTableAssociatePrivateSubnet02:
Type: AWS::EC2::SubnetRouteTableAssociation
Properties:
SubnetId: !Ref PrivateSubnet02
RouteTableId: !Ref RouteTable
CustomerGateway:
Type: AWS::EC2::CustomerGateway
Properties:
BgpAsn: 65000
IpAddress: !Ref PublicIP
Type: ipsec.1
Tags:
- Key: Name
Value: VPN AWS & on prem
VirtualPrivateGateway:
Type: AWS::EC2::VPNGateway
Properties:
AmazonSideAsn: 64512
Tags:
- Key: Name
Value: VPN AWS & on prem
Type: ipsec.1
AttachVirtualPrivateGatewayToVPC:
Type: AWS::EC2::VPCGatewayAttachment
Properties:
VpcId: !Ref VPC
VpnGatewayId: !Ref VirtualPrivateGateway
VPNConnection:
Type: AWS::EC2::VPNConnection
Properties:
CustomerGatewayId: !Ref CustomerGateway
StaticRoutesOnly: true
VpnGatewayId: !Ref VirtualPrivateGateway
Type: ipsec.1
Tags:
- Key: Name
Value: VPN AWS & on prem
AttachRouteToVPNConnection:
Type: AWS::EC2::VPNConnectionRoute
Properties:
DestinationCidrBlock: !Ref OnPremiseSubnet
VpnConnectionId: !Ref VPNConnection
PropagateOnPremiseSubnetToRouteTable:
Type: AWS::EC2::VPNGatewayRoutePropagation
DependsOn:
- AttachVirtualPrivateGatewayToVPC
Properties:
RouteTableIds:
- !Ref RouteTable
VpnGatewayId: !Ref VirtualPrivateGateway/ip firewall filter
add action=accept chain=input comment="AWS VPN Frankfurt IPSec" dst-port=500,4500 \
protocol=udp
/ip ipsec profile
add dh-group=modp1024 dpd-interval=10s dpd-maximum-failures=3 enc-algorithm=\
aes-128 lifetime=8h name=aws-vpn-frankfurt-ipsec-profile
/ip ipsec peer
add address=TUNNEL_OUTSIDE_IP/32 comment="AWS VPN Frankfurt IPSec" local-address=YOUR_PUBLIC_IP name=aws-vpn-frankfurt-ipsec-peer \
profile=aws-vpn-frankfurt-ipsec-profile
/ip ipsec proposal
add comment="AWS VPN Frankfurt IPSec" enc-algorithms=aes-128-cbc lifetime=1h name=aws-vpn-frankfurt-ipsec-proposal
/ip ipsec identity
add peer=aws-vpn-frankfurt-ipsec-peer comment="AWS VPN Frankfurt IPSec" secret=SECRET_HERE
/ip ipsec policy
add dst-address=10.1.10.0/24 comment="AWS VPN Frankfurt IPSec" peer=aws-vpn-frankfurt-ipsec-peer proposal=\
aws-vpn-frankfurt-ipsec-proposal sa-dst-address=TUNNEL_OUTSIDE_IP sa-src-address=\
YOUR_PUBLIC_IP src-address=192.168.88.0/24 tunnel=yes